rancher版本:v1.28.6
集群操作系统: debian12
集群版本:v1.26.15+k3s1
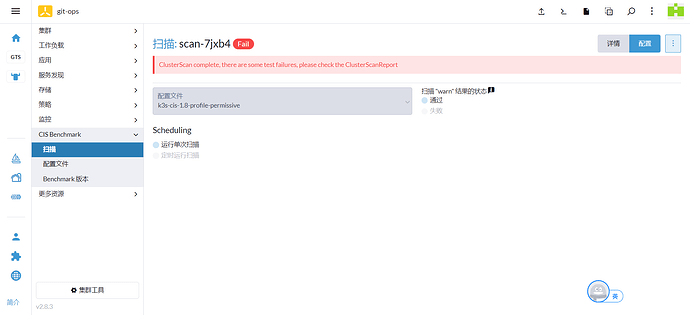
创建扫描后报错.下载查看了报告大概是说没有权限.这个新接触不太懂.望指导一下
报告日志太长截取头尾
| id | description | remediation | state | node_type |
|---|---|---|---|---|
| 1.1.1 | Ensure that the API server pod specification file permissions are set to 600 or more restrictive (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chmod 600 $apiserverconf Not Applicable. |
mixed | master |
| 1.1.2 | Ensure that the API server pod specification file ownership is set to root:root (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chown root:root $apiserverconf Not Applicable. |
mixed | master |
| 1.1.3 | Ensure that the controller manager pod specification file permissions are set to 600 or more restrictive (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chmod 600 $controllermanagerconf Not Applicable. |
mixed | master |
| 1.1.4 | Ensure that the controller manager pod specification file ownership is set to root:root (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chown root:root $controllermanagerconf Not Applicable. |
mixed | master |
| 1.1.5 | Ensure that the scheduler pod specification file permissions are set to 600 or more restrictive (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chmod 600 $schedulerconf Not Applicable. |
mixed | master |
| 1.1.6 | Ensure that the scheduler pod specification file ownership is set to root:root (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chown root:root $schedulerconf Not Applicable. |
mixed | master |
| 1.1.7 | Ensure that the etcd pod specification file permissions are set to 600 or more restrictive (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chmod 600 $etcdconf Not Applicable. |
mixed | master |
| 1.1.8 | Ensure that the etcd pod specification file ownership is set to root:root (Automated) | Run the below command (based on the file location on your system) on the control plane node. For example, chown root:root $etcdconf Not Applicable. |
mixed | master |
| 5.3.2 | Ensure that all Namespaces have NetworkPolicies defined (Manual) | Follow the documentation and create NetworkPolicy objects as you need them. Permissive - Enabling Network Policies can prevent certain applications from communicating with each other. |
mixed | node |
| — | — | — | — | — |
| 5.4.1 | Prefer using Secrets as files over Secrets as environment variables (Manual) | If possible, rewrite application code to read Secrets from mounted secret files, rather than from environment variables. |
mixed | node |
| 5.4.2 | Consider external secret storage (Manual) | Refer to the Secrets management options offered by your cloud provider or a third-party secrets management solution. |
mixed | node |
| 5.5.1 | Configure Image Provenance using ImagePolicyWebhook admission controller (Manual) | Follow the Kubernetes documentation and setup image provenance. |
mixed | node |
| 5.7.1 | Create administrative boundaries between resources using namespaces (Manual) | Follow the documentation and create namespaces for objects in your deployment as you need them. |
mixed | node |
| 5.7.2 | Ensure that the seccomp profile is set to docker/default in your Pod definitions (Manual) | Use securityContext to enable the docker/default seccomp profile in your pod definitions.An example is as below: securityContext: seccompProfile: type: RuntimeDefault |
mixed | node |
| 5.7.3 | Apply SecurityContext to your Pods and Containers (Manual) | Follow the Kubernetes documentation and apply SecurityContexts to your Pods. For a suggested list of SecurityContexts, you may refer to the CIS Security Benchmark for Docker Containers. |
mixed | node |
| 5.7.4 | The default namespace should not be used (Manual) | Ensure that namespaces are created to allow for appropriate segregation of Kubernetes resources and that all new resources are created in a specific namespace. Permissive - Kubernetes provides a default namespace. |
mixed | node |