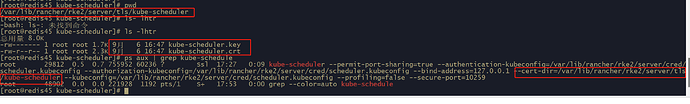
[root@redis45 server]# ls -lhtr tls
总用量 112K
-rw------- 1 root root 227 9月 6 2023 client-ca.key
-rw-r–r-- 1 root root 570 9月 6 2023 client-ca.crt
-rw------- 1 root root 227 9月 6 2023 server-ca.key
-rw-r–r-- 1 root root 570 9月 6 2023 server-ca.crt
-rw------- 1 root root 227 9月 6 2023 request-header-ca.key
-rw-r–r-- 1 root root 595 9月 6 2023 request-header-ca.crt
-rw------- 1 root root 1.7K 9月 6 2023 service.key
drwx------ 2 root root 6 9月 6 2023 temporary-certs
drwxr-xr-x 2 root root 76 9月 6 2023 kube-controller-manager
drwxr-xr-x 2 root root 58 9月 6 2023 kube-scheduler
-rw------- 1 root root 227 8月 7 08:58 client-admin.key
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-admin.crt
-rw------- 1 root root 227 8月 7 08:58 client-controller.key
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-controller.crt
-rw------- 1 root root 227 8月 7 08:58 client-scheduler.key
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-scheduler.crt
-rw------- 1 root root 227 8月 7 08:58 client-kube-apiserver.key
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-kube-apiserver.crt
-rw------- 1 root root 227 8月 7 08:58 client-kube-proxy.key
-rw------- 1 root root 227 8月 7 08:58 client-rke2-controller.key
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-kube-proxy.crt
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-rke2-controller.crt
-rw------- 1 root root 227 8月 7 08:58 client-rke2-cloud-controller.key
-rw------- 1 root root 227 8月 7 08:58 client-kubelet.key
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-rke2-cloud-controller.crt
-rw------- 1 root root 227 8月 7 08:58 serving-kube-apiserver.key
-rw------- 1 root root 227 8月 7 08:58 serving-kubelet.key
-rw-r–r-- 1 root root 1.4K 8月 7 08:58 serving-kube-apiserver.crt
-rw------- 1 root root 227 8月 7 08:58 client-auth-proxy.key
-rw-r–r-- 1 root root 1.2K 8月 7 08:58 client-auth-proxy.crt
drwxr-xr-x 2 root root 232 8月 7 08:58 etcd
-rw-r–r-- 1 root root 2.9K 8月 7 08:58 dynamic-cert.json
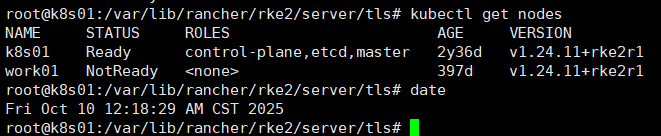
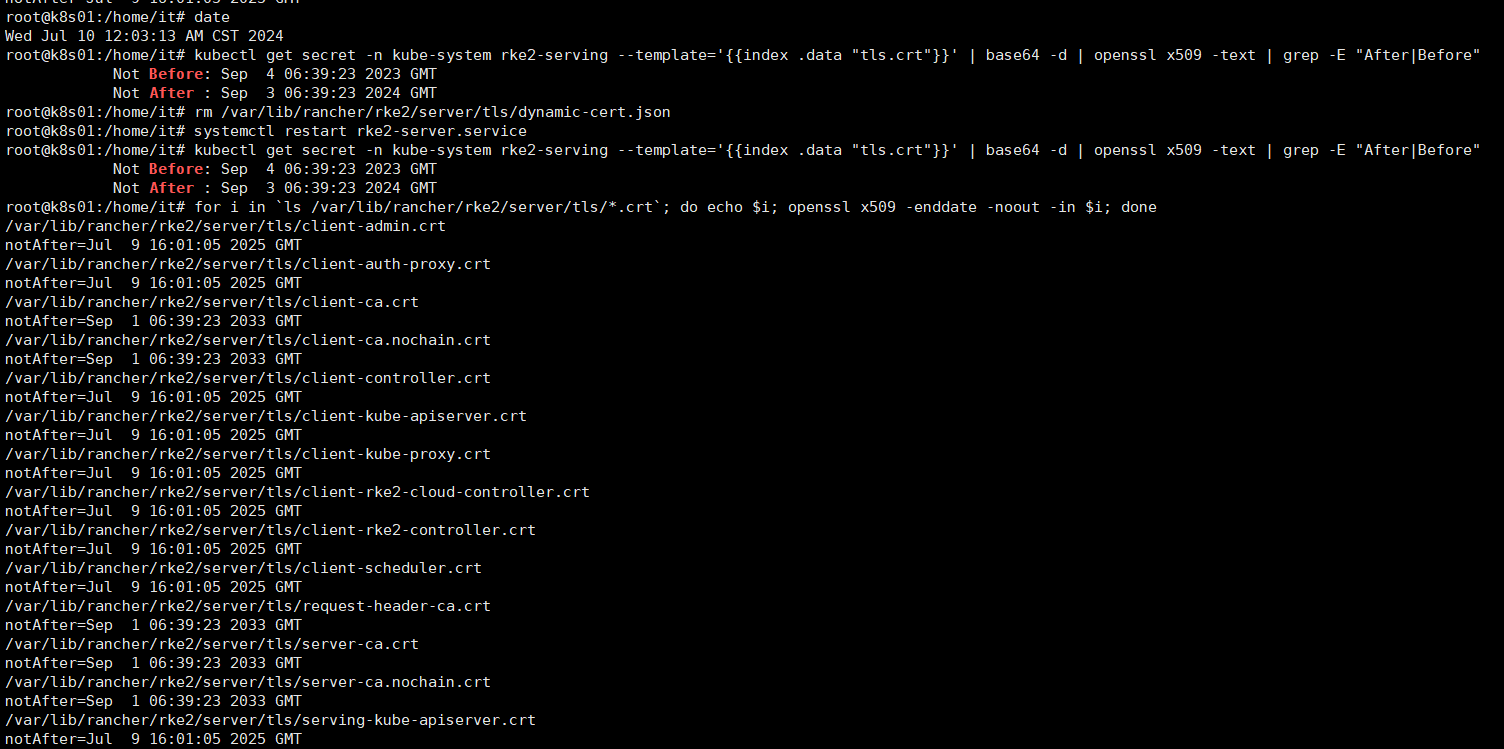
[root@redis45 server]# date
2024年 08月 07日 星期三 09:00:01 CST
[root@redis45 server]# ls -lhtr tls/kube-scheduler/
总用量 8.0K
-rw------- 1 root root 1.7K 9月 6 2023 kube-scheduler.key
-rw-r–r-- 1 root root 2.3K 9月 6 2023 kube-scheduler.crt
[root@redis45 server]# ls -lhtr tls/kube-controller-manager/
总用量 8.0K
-rw------- 1 root root 1.7K 9月 6 2023 kube-controller-manager.key
-rw-r–r-- 1 root root 2.3K 9月 6 2023 kube-controller-manager.crt
[root@redis45 server]# date
2024年 10月 07日 星期一 08:57:37 CST
[root@redis45 server]#
查看日志 tail -f /var/log/message
Oct 7 08:59:06 redis45 rancher-system-agent[12862]: time=“2024-10-07T08:59:06+08:00” level=debug msg="[Prober] (calico) writing probe status to map"
Oct 7 08:59:06 redis45 rancher-system-agent[12862]: time=“2024-10-07T08:59:06+08:00” level=debug msg=“Probe output was Get “https://127.0.0.1:10259/healthz”: x509: certificate has expired or is not yet valid: current time 2024-10-07T08:59:06+08:00 is after 2024-09-05T07:47:14Z”
Oct 7 08:59:06 redis45 rancher-system-agent[12862]: time=“2024-10-07T08:59:06+08:00” level=debug msg=“Setting success threshold to 1”
Oct 7 08:59:06 redis45 rancher-system-agent[12862]: time=“2024-10-07T08:59:06+08:00” level=debug msg=“Setting failure threshold to 2”
Oct 7 08:59:06 redis45 rancher-system-agent[12862]: time=“2024-10-07T08:59:06+08:00” level=debug msg=“Probe failed”
Oct 7 08:59:06 redis45 rancher-system-agent[12862]: time=“2024-10-07T08:59:06+08:00” level=debug msg="[Prober] (kube-scheduler) writing probe status to map"
Oct 7 08:59:06 redis45 rancher-system-agent[12862]: time=“2024-10-07T08:59:06+08:00” level=debug msg=“Probe output was Get “https://127.0.0.1:10257/healthz”: x509: certificate has expired or is not yet valid: current time 2024-10-07T08:59:06+08:00 is after 2024-09-05T07:47:14Z”